Let’s take a closer look at cloning a NexKey RFID access card. Unfortunately, our steps for cloning HID tags won’t generalize. The NexKey protocol is rarer and locked in a more comprehensive security package. The Proxmark tooling has less functionality for NexKeys so prepare to get scrappy.
We start by reading the card and the demodulated signal. Notice the NexKey tag stores the data in the NexWatch ID (64923010) and the Demodulated Buffer. Unlike the HID tag, there’s no encoded Facility Code + Card Number. How do we extract the NexWatch ID from the demodulated buffer? Once we have the NexWatch ID, how do we clone the card?

Unfortunately, NexKey tags aren’t well supported by Proxmark tooling. Some intrepid searching on the Proxmark forum helps us uncover how to decode the NexKey bit pattern. The two key pieces of information we need are the bit pattern data format (Image 3) and the encoding for the NexWatch ID (Image 4).
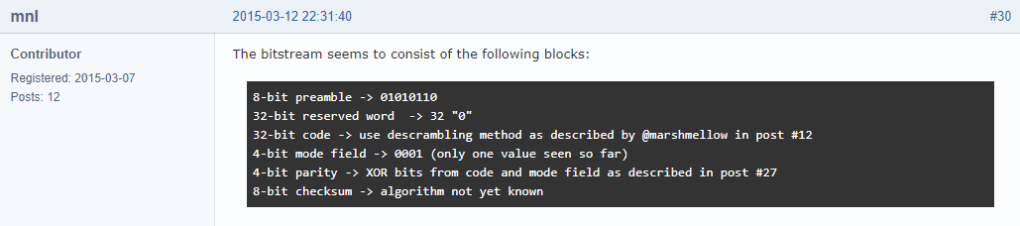

In brief: 1) reverse the demodulated raw bit pattern, 2) index subset the 32bit UID from the reversed raw bit pattern, 3) descramble the 32bit UID, 4) convert the descrambled 32bit UID to decimal to recover the NexWatch ID.
Talk is cheap. Show me an example.
- We start with the raw demodulated bit pattern: 10101001111111111111111111111111111111111000101111011011101110010010010111100001011100011111111111111111111111111111111111111111
- Reversing the bit pattern gives a preamble, reserved word, UID, mode field, parity check, and checksum: 01010110000000000000000000000000000000000111010000100100010001101101101000011110100011100000000000000000000000000000000000000000
- Descramble the UID and convert to decimal to get the NexWatch ID 01110100001001000100011011011010 -> 00000011110111101010010110000010 -> 64923010
To clone the NexKey, we can’t just copy over the NexWatch ID into the target card. The NexKey’s data format is natively compatible with a T5577 format and will require copying over individual blocks of the T5577 raw data. The page 0, block 0-3 data dumps contain all the information needed to clone the NexKey. All we need to do is write these 4 blocks into the target T5577. Nice!
