Yesterday I wrote a demonstrative example of cloning an unencrypted HID RFID access card. You might complain that it was exercise in Proxmark magical keyboard incantations. Well buckle up reader – today we dive into the details.
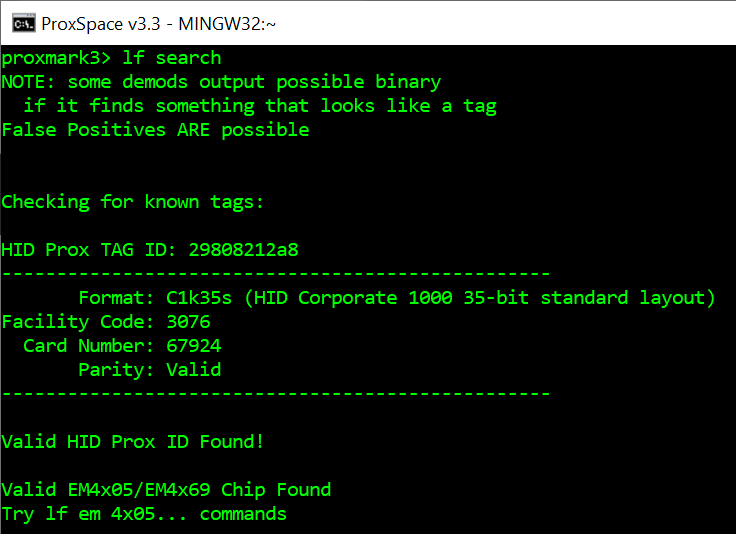
The above screenshot (Image 1) shows the results of reading our HID card. When cloning this card, we just need to write the HID Prox TAG ID into a protocol compatible card. The TAG ID is a unique identifier for this card that encodes both the Facility Code and Card Number.
How did we get the TAG ID and how does the encoding work?
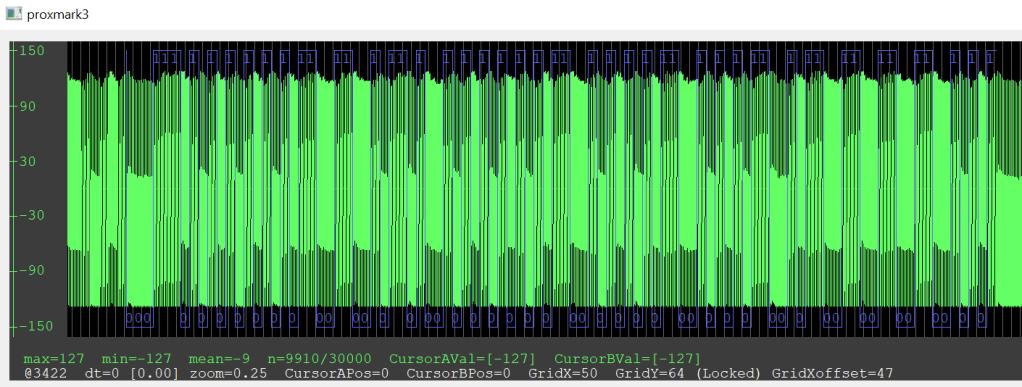
We start with the raw low frequency signal wave (Image 2) picked up by the Proxmark antenna when reading the tag. Notice the blue signal conveniently demodulated from the wave pattern to form our raw 96-bit pattern. These raw bits, combined with knowledge of the HID 35-bit formatting layout, can be transformed into the TAG ID. The configuration settings and data formats are hidden in plain sight in the Proxmark developer forum.
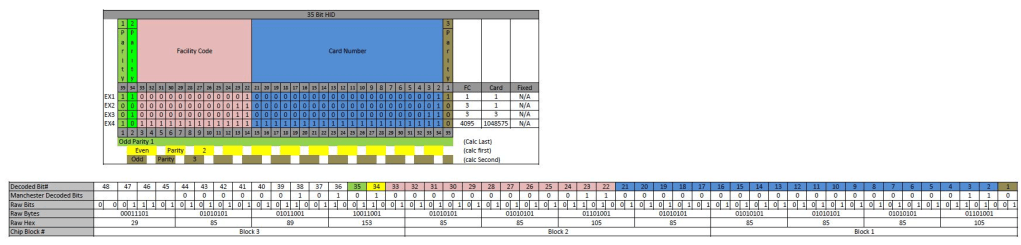
The below schematic (Image 3) shows the detailed configuration setting for interpreting the raw bit pattern. In brief: 1) perform a Manchester decoding on the raw 96bit pattern, 2) index subset the 48-bit decoded bit pattern into Facility Code bits and Card Number bits, 3) strip the preamble bits to form the unique Tag ID.
Talk is cheap. Show me an example.
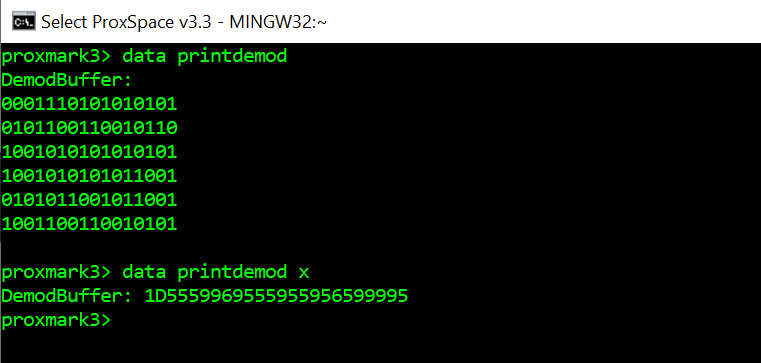
We start with the raw demodulated bit pattern (Image 2) which the DemodBuffer conveniently expresses in binary and hex (Image 4).
The manchester decoding gives: 001000000010100110000000100000100001001010101000
We separate the manchester decoded bits into a preamble, Facility Code, and Card Number.
Converting from binary to decimal gives the Facility Code (110000000100 -> 3076) and Card Number (00010000100101010100 -> 67924).
Removing the preamble and converting the remaining bit pattern from binary to hex gives the TAG ID (00000010100110000000100000100001001010101000 -> 29808212a8).
From the raw bit pattern, we were able to recover the TAG ID (3076), Facility Code (67924), and Card Number (29808212a8). You can verify this yourself using an online Wiegand calculator. Pretty neat!
Pingback: Day 18: NexKey Deep Dive – Erick's Blog